Send Email Using Telnet sets the stage for this enthralling narrative, offering readers a glimpse into a fascinating, albeit outdated, method of email communication. We’ll explore the historical context of Telnet, its practical application for sending emails, and critically examine its security implications. Prepare to delve into the world of command-line email, contrasting this method with modern email protocols like SMTP.
This exploration will cover everything from configuring a Telnet client for email to constructing the actual email messages. We’ll navigate the intricacies of Telnet commands, examine the formatting of email headers and bodies, and even delve into the process of sending attachments. Expect practical examples, detailed procedures, and a critical comparison of Telnet with modern email methods. Security concerns will also be addressed, highlighting the potential risks and necessary precautions.
Introduction to Telnet Email Sending
Telnet, a network protocol, has a rich history in facilitating text-based communication. While its role in email is now largely obsolete, understanding its past use provides context for modern email protocols. This exploration delves into the historical context, security concerns, and a comparison between Telnet and contemporary email protocols.Telnet, in its basic form, establishes a connection between a client and a server.
This connection allows for bidirectional text-based communication. In the context of email, Telnet was employed to send emails by providing a text-based interface to interact with email servers. This involved crafting and sending emails through commands, much like interacting with a command-line interface.
Historical Context and Significance
Telnet’s significance in the early days of computer networking was substantial. It provided a fundamental way to access and control remote systems, which was critical in a time when graphical user interfaces were less prevalent. Telnet was essential for remote administration, file transfer, and other networking tasks, including email. Its ubiquity made it a critical tool for the early adoption of the internet and networking technologies.
Security Implications of Telnet for Email
Using Telnet for email transmission poses significant security risks. Telnet is a clear-text protocol, meaning that all data transmitted, including usernames and passwords, is sent unencrypted. This vulnerability makes it susceptible to eavesdropping, and easily compromised by malicious actors. Any interception of the transmission could lead to unauthorized access to email accounts, data breaches, and potential financial or reputational damage.
Comparison of Telnet and Modern Email Protocols
| Feature | Telnet | SMTP (Simple Mail Transfer Protocol) |
|---|---|---|
| Protocol Type | Clear-text | Secure (with TLS/SSL) or clear-text |
| Security | Highly vulnerable to eavesdropping and interception | Secure versions (TLS/SSL) significantly reduce security risks. |
| Authentication | Often handled with separate mechanisms (e.g., password prompts) | Authentication mechanisms built directly into the protocol. |
| Complexity | Requires command-line interaction, potentially more complex | More automated and integrated, simplifying email sending. |
| Usage Today | Rarely used for email | Widely used for sending and receiving email. |
This table highlights the fundamental differences between Telnet and modern email protocols like SMTP. SMTP’s inherent security enhancements and user-friendliness, especially with TLS/SSL, contrast starkly with the vulnerabilities inherent in Telnet.
Configuring Telnet for Email: Send Email Using Telnet
Telnet, while a powerful tool for network communication, requires careful configuration to send emails. This involves understanding the protocols, servers, and necessary settings specific to your email provider. Incorrect configurations can lead to failed connections or authentication issues. This guide details the essential steps for configuring a Telnet client to send emails.
Connecting to the Email Server
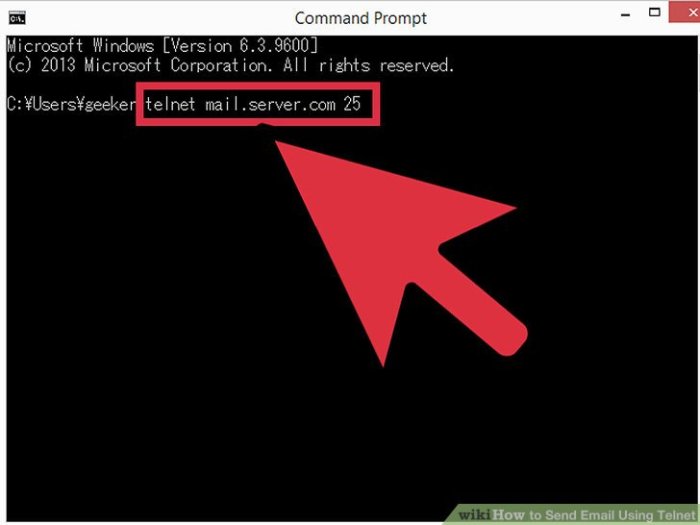
Successfully sending emails via Telnet hinges on establishing a connection to the correct email server. This involves specifying the server’s address and the appropriate port number. Different email providers use different servers. The address and port are crucial to the connection process.
- Obtain the email server’s address. This information is typically provided by your email provider.
- Identify the correct port number. The default Telnet port for SMTP is 25, but some providers use alternative ports. Consult your provider’s documentation for the precise port number.
- Open your Telnet client and enter the server address and the designated port number. This initiates the connection.
Authentication
Securely sending emails requires authentication to verify your identity. This typically involves entering your email address and password. The process differs slightly depending on the email provider.
So, I was digging into old tech manuals today, and stumbled upon this fascinating method for sending emails using Telnet. It’s surprisingly complex, but hey, it’s kind of like a forgotten language. Speaking of interesting announcements, did you hear about Post Malone’s tour with Swae Lee? Post Malone announces tour with Swae Lee is a huge deal! Getting back to the topic, mastering Telnet email might not be a priority these days, but it’s cool to see how things have evolved.
I guess sending emails via command line is definitely a throwback.
- Enter your email address as prompted by the Telnet client.
- Enter your email password as prompted. Be extremely cautious about entering your password in plain text. Use secure methods for storing and managing your passwords.
Email Server Port Configurations
Different email providers use various port numbers for Telnet SMTP connections. The table below provides a general overview of common port numbers. Note that these aregeneral* configurations, and your specific provider might use a different port. Always refer to your provider’s documentation for the accurate configuration.
| Email Provider | Typical Telnet Port |
|---|---|
| Gmail | 587 (often used with TLS/SSL) |
| Yahoo Mail | 587 (often used with TLS/SSL) |
| Outlook.com | 587 (often used with TLS/SSL) |
| Other Providers | Consult your provider’s documentation |
Important Considerations
Telnet, while functional, is less secure than modern methods for email transmission. For enhanced security, consider using Secure Sockets Layer (SSL) or Transport Layer Security (TLS) when connecting to your email server. These protocols encrypt the communication, making it more resistant to eavesdropping. Using TLS/SSL is often the recommended method.
Constructing Email Messages using Telnet
Sending emails via Telnet requires a specific format. This format differs significantly from graphical email clients, and understanding its structure is crucial for successful transmission. You’ll need to craft the message meticulously, adhering to the protocol’s guidelines.The Telnet protocol uses commands and data to interact with the email server. Email messages, therefore, aren’t simply typed in like a text document.
Instead, they are broken down into headers and a body, each with its own format and specific information.
Email Message Format
The structure of an email message sent via Telnet is divided into headers and the body. Headers contain metadata about the email, such as sender, recipient, subject, and date. The body contains the actual content of the message. This structured approach ensures the email server can process and route the message correctly.
Email Headers
Headers provide critical information for email routing and handling. They are crucial for the server to understand the message’s origin, destination, and other important attributes. The order of headers matters, as the server parses them sequentially.
- The “From:” header specifies the sender’s email address. It is essential for the recipient to know who sent the message.
- The “To:” header specifies the recipient’s email address. This tells the server where to deliver the message.
- The “Subject:” header provides a brief description of the email’s content. A clear subject helps recipients prioritize and categorize messages.
- The “Date:” header indicates when the email was sent. This is useful for tracking and managing email correspondence.
Constructing the Email Body
The email body contains the actual message content. It is composed of the text you want to convey to the recipient. The format is straightforward, typically just plain text. Formatting options are limited compared to graphical email clients.
- The body is entered after all the headers. It follows the headers directly, and the server expects a blank line to signal the end of the headers and the beginning of the message content.
- Use plain text for the body. Avoid HTML formatting or special characters not supported by the server. The body is typically treated as simple text, and complex formatting will not render correctly.
Examples of Telnet Email Messages
Here are examples of complete email messages structured for Telnet transmission. These demonstrate the correct syntax for headers and the body.
| Header | Example Value |
|---|---|
| From: | [email protected] |
| To: | [email protected] |
| Subject: | Important Announcement |
| Date: | Mon, 10 Oct 2023 10:00:00 -0700 |
Example Email Body:
Dear Recipient,
This is an important announcement.
Please review the attached document.
Sincerely,
Sender
Complete Example (showing headers and body):
From: [email protected]
To: [email protected]
Subject: Important Announcement
Date: Mon, 10 Oct 2023 10:00:00 -0700Dear Recipient,
This is an important announcement.
Please review the attached document.
Sincerely,
Sender
Methods and Procedures
Sending emails via Telnet requires a structured approach. This section details the common commands, attachment handling, error management, and disconnection procedures for a secure and effective email transmission process. Understanding these methods is crucial for anyone seeking to automate email tasks using Telnet.Telnet, while a powerful tool, can be complex for beginners. Carefully following the procedures Artikeld below will help ensure successful email transmissions and minimize potential errors.
Common Telnet Commands for Email Actions
Telnet offers a range of commands for interacting with email servers. These commands allow for various actions, from sending messages to retrieving mail. A basic understanding of these commands is essential for email management using Telnet.
- HELO/EHLO: Initiates a connection with the mail server. This command is crucial for establishing communication and authentication.
- MAIL FROM: Specifies the sender’s email address.
- RCPT TO: Specifies the recipient’s email address.
- DATA: Indicates the start of the message body.
- . (dot): Signals the end of the message body. Crucially, this marks the completion of the email transmission.
- QUIT: Terminates the Telnet session with the mail server.
Sending Attachments via Telnet
Sending attachments using Telnet requires a specific procedure. This method is less intuitive than modern email clients, but it’s a vital skill for users familiar with Telnet.
- Identify the Attachment: The first step is to identify the file to be attached. This involves specifying the file path and name.
- Encoding the Attachment: The attachment needs to be encoded. This typically involves converting the file into a format readable by the mail server. This may involve base64 encoding, or other methods.
- Include Attachment in the Message Body: The encoded attachment content needs to be inserted into the email message body. This insertion needs to be formatted in a way the server understands.
- Send the Email: Using the Telnet commands Artikeld previously, send the message, including the encoded attachment.
Handling Email Errors During Transmission
Error handling is essential during Telnet-based email transmission. Different errors can occur, and understanding their causes and solutions is crucial.
- Connection Failures: The connection to the mail server might fail due to network issues or server unavailability. Verify network connectivity and server status.
- Syntax Errors: Incorrect Telnet commands or improperly formatted messages can cause syntax errors. Ensure adherence to the email server’s protocol.
- Recipient Errors: The recipient’s email address may be invalid or the server may reject the message for other reasons. Verify recipient addresses and server policies.
- Server Errors: The mail server may reject the message due to internal errors. Review the server’s error messages for guidance.
Disconnecting from the Email Server
Proper disconnection is essential to maintain a stable connection and prevent data loss. Incorrect disconnection can lead to incomplete transactions or even data corruption.
- Using the QUIT Command: The `QUIT` command is the standard way to close the Telnet session with the mail server. This ensures a clean disconnection.
Security Considerations
Sending email via Telnet, while functional, presents significant security vulnerabilities. The protocol itself is unencrypted, making all transmitted data susceptible to interception and manipulation by malicious actors. This inherent lack of security renders Telnet-based email transmission unsuitable for sensitive or confidential information.
Telnet’s Vulnerability to Interception
Telnet is an unencrypted protocol. This means any data exchanged, including usernames, passwords, and the email content itself, can be easily intercepted by third parties. A malicious actor monitoring the network can gain access to this sensitive information. This poses a considerable risk to individuals and organizations handling confidential email correspondence.
Ever wondered how to send emails using Telnet? It’s a surprisingly versatile tool, and while not the most user-friendly method, it can be surprisingly useful. If you’re looking to launch a business, say, like a Start a Drop Shipping Business , knowing how to send emails using Telnet might come in handy for automation or scripting tasks.
Knowing these technical skills can be a real asset, and that’s something to remember when building a business. In the end, Telnet’s simplicity for sending emails is a fascinating bit of history.
Risks of Insecure Telnet Connections
The absence of encryption in Telnet makes it extremely vulnerable to various security threats. These threats include eavesdropping, where unauthorized individuals can intercept sensitive information; man-in-the-middle attacks, where an attacker intercepts and modifies communication between two parties; and data tampering, where an attacker modifies the content of the email. These risks are compounded by the lack of authentication mechanisms, making it a target for unauthorized access.
Importance of Strong Passwords and Authentication
Strong passwords and robust authentication mechanisms are critical for any email system, especially when using a protocol like Telnet. Weak passwords can be easily cracked, allowing unauthorized access to email accounts and potentially compromising sensitive information. Multi-factor authentication (MFA) adds an extra layer of security, requiring multiple forms of verification before granting access.
Secure Alternatives to Telnet
Several secure alternatives to Telnet exist for email transmission. These methods employ encryption to protect data during transit, significantly reducing the risk of interception and unauthorized access. Secure Shell (SSH) is a popular alternative, providing a secure channel for remote access and commands, including email transmission. Other secure methods include using email clients with built-in encryption capabilities or utilizing dedicated secure email gateways.
- SSH (Secure Shell): SSH offers encrypted communication channels, protecting sensitive data from eavesdropping and tampering. This provides a significantly safer alternative to Telnet for email transmission, preventing malicious actors from intercepting or modifying email content.
- SMTP (Simple Mail Transfer Protocol) with TLS/SSL: Using SMTP with Transport Layer Security (TLS) or Secure Sockets Layer (SSL) encryption encrypts the communication between the mail client and the mail server. This prevents interception and ensures the confidentiality of email messages.
- Dedicated Secure Email Gateways: These specialized systems offer robust security measures, often including advanced threat detection and prevention capabilities. They are a common choice for organizations needing a high level of email security.
Practical Examples
Telnet, while not the most user-friendly method for email, provides a fundamental understanding of the underlying communication protocols. These examples illustrate the process of sending emails, handling attachments, and troubleshooting potential issues encountered during Telnet email sessions. They highlight the necessity of precise commands and error handling in this less intuitive environment.Understanding these practical examples is crucial for troubleshooting and maintaining email systems.
Knowing how to interpret Telnet responses and commands allows for more effective problem-solving in network environments.
Simple Message Sending
Telnet email sessions for sending simple messages require precise syntax. The following illustrates a typical session:
OPEN smtp.example.com 25
EHLO example.com
MAIL FROM: [email protected]
RCPT TO: [email protected]
DATA
Subject: Hello
This is a simple test message.
.
QUIT
This example demonstrates the core commands needed to establish a connection, authenticate, and send a simple message. Each command is critical for the process. Notice the use of `.` to signal the end of the message body.
Sending Email with Attachments
Sending emails with attachments via Telnet is more complex than simple messages. It necessitates encoding the attachment into the message body. This process is often error-prone and requires meticulous attention to detail.
OPEN smtp.example.com 25
EHLO example.com
MAIL FROM: [email protected]
RCPT TO: [email protected]
DATA
Subject: Attachment Test
This is a test email with an attachment.
Content-Type: application/octet-stream; name="attachment.txt"
Content-Transfer-Encoding: base64
[Encoded attachment data here]
.
QUIT
This example shows the general structure, but the crucial step is encoding the attachment into base64 or other suitable formats.
Handling Telnet Email Errors
Telnet email sessions can produce various errors. Understanding these errors is essential for troubleshooting. Common errors include incorrect syntax, authentication failures, and connection issues.
OPEN smtp.example.com 25
EHLO example.com
MAIL FROM: [email protected]
RCPT TO: [email protected]
In this example, the recipient address `[email protected]` might produce an error message like “550 Requested mail action not allowed.” Analyzing the error messages is crucial for determining the issue and taking corrective actions.
Connection and Disconnection Procedures
Establishing and terminating a Telnet email session involves specific commands. The `OPEN` command initiates the connection, and `QUIT` terminates it.
- The `OPEN` command initiates the connection to the specified SMTP server on port 25. Incorrect port numbers or server addresses will result in connection failures.
- The `EHLO` command, if supported, is essential for authentication and negotiation of email features. Failure to use this command correctly could lead to authentication errors or rejection of the message.
- The `QUIT` command closes the connection gracefully, ensuring all outstanding data is sent. Failing to use this command might leave the connection open, consuming resources.
Limitations and Alternatives
Telnet, while functional for sending emails, suffers from significant limitations in the modern digital landscape. Its lack of security and cumbersome setup make it impractical for most use cases. This section explores the shortcomings of Telnet-based email and introduces more secure and efficient alternatives.
Limitations of Telnet for Email Communication
Telnet, a protocol relying on plain text, exposes email data in an unencrypted form. This vulnerability makes it susceptible to eavesdropping and interception, posing a serious risk to sensitive information. The protocol’s inherent lack of authentication mechanisms also leaves it open to unauthorized access. Furthermore, Telnet’s command-line interface (CLI) approach is complex and not user-friendly, making it challenging to implement compared to graphical email clients.
Learning how to send email using Telnet is a surprisingly useful skill, though perhaps not as exciting as grafting a fruit tree. Graft a Fruit Tree might be a more visually appealing project, but understanding the technical side of email transmission is crucial. This knowledge, like the meticulous care needed for successful grafting, provides a solid foundation for more complex network tasks.
Ultimately, mastering Telnet for email is a valuable tool in your digital toolkit.
Finally, Telnet’s limited functionality doesn’t support advanced features like attachments or complex message formatting, making it unsuitable for modern email needs.
Modern Alternatives to Telnet
Several secure and user-friendly alternatives to Telnet for sending emails exist. These protocols prioritize security, user experience, and advanced functionalities. Popular options include SMTP (Simple Mail Transfer Protocol), which is the standard protocol for email transmission. Other methods such as dedicated email client software and webmail platforms are also readily available, and often more suitable for users.
Advantages and Disadvantages of Modern Alternatives
| Alternative | Advantages | Disadvantages |
|---|---|---|
| SMTP | Industry standard, widely supported by email servers, generally faster and more efficient than Telnet. Supports advanced features like attachments and message formatting. | Requires server configuration and potentially complex setup. Security vulnerabilities still exist if not properly secured. |
| Email Clients (e.g., Outlook, Thunderbird) | User-friendly interface, intuitive design, supports advanced features like message management, organization, and attachments. Offers greater security options via encryption and authentication. | Requires installation and configuration on the user’s machine. Might not be suitable for automated email tasks or scripts. |
| Webmail Platforms (e.g., Gmail, Outlook.com) | Accessible from any device with internet connectivity. Provides a centralized platform for managing multiple accounts. Usually offers user-friendly interface and security measures. | Reliance on internet connection. Security depends on the platform’s security measures. Potential for data breaches if not handled securely. |
Comparison of Telnet with Secure Alternatives
The following table provides a comparative analysis of Telnet’s limitations against secure alternatives.
| Feature | Telnet | SMTP | Email Client | Webmail |
|---|---|---|---|---|
| Security | Low (unencrypted data transmission) | Moderate (depends on server configuration) | High (often supports encryption and authentication) | High (depends on platform security) |
| Ease of Use | Low (CLI based) | Moderate (requires configuration) | High (user-friendly interface) | High (accessible from any device) |
| Functionality | Limited (basic email transfer) | High (supports attachments, formatting) | High (supports advanced features) | High (centralized management) |
| Scalability | Low | High | High | High |
Illustrative Scenarios
Telnet email, while a historical method, still finds niche applications in specific environments. Understanding when Telnet is appropriate, and when modern protocols are better suited, is crucial for effective email management. This section details scenarios where Telnet’s functionality might be preferable, contrasting it with situations where more robust, contemporary protocols are the better choice.
Suitable Environments for Telnet Email, Send Email Using Telnet
Telnet email, due to its simplicity, remains useful in environments with limited resources or specific requirements. These situations often involve older systems or specialized applications that may not be easily integrated with modern email clients.
- Legacy Systems: Organizations with large numbers of legacy systems that are not easily upgraded or do not support modern protocols may find Telnet email a more practical solution for maintaining communication between these systems.
- Automated Processes: Scripting email tasks within a tightly controlled environment, such as a server farm or automated data processing system, can be streamlined using Telnet’s command-line interface.
- Security-Focused Environments: Certain highly secure environments, where strict control over email transmission is needed, might leverage Telnet’s direct interaction for specific communications, potentially avoiding intermediate mail servers.
Modern Email Protocols Preferred
Modern email protocols, such as SMTP (Simple Mail Transfer Protocol), offer significant advantages over Telnet for email transmission. These protocols have evolved to address security, scalability, and reliability challenges.
- Security Enhancements: Modern protocols support encryption (e.g., TLS/SSL) to protect email content during transmission, mitigating risks associated with data interception.
- Scalability and Reliability: Modern protocols are designed for high-volume email exchanges, handling large datasets and numerous recipients efficiently and reliably.
- Integration with Modern Systems: Modern email clients and systems are built to work seamlessly with standard protocols, minimizing integration complexities.
Choosing the Appropriate Protocol
Selecting the appropriate protocol for email transmission depends on the specific needs of the environment. Careful consideration of factors like security requirements, system compatibility, and the volume of email traffic is crucial.
- Security Considerations: If security is paramount, modern protocols with encryption are essential. Telnet, lacking built-in security mechanisms, is not suitable in high-security environments.
- System Compatibility: Evaluate if the existing systems and applications can be integrated with modern protocols without substantial modification or investment.
- Volume and Frequency: For high-volume email exchanges, modern protocols offer superior scalability and efficiency, while Telnet might struggle under heavy load.
End of Discussion
In conclusion, while Telnet email might seem archaic in today’s digital landscape, understanding its functionality provides a valuable perspective on the evolution of email communication. This detailed exploration reveals both the practical aspects and significant security vulnerabilities of this method. We’ve explored its configuration, message construction, and procedures, and ultimately, the limitations and modern alternatives to this older approach.
Hopefully, this comprehensive guide will provide a solid understanding of Send Email Using Telnet and its place in the broader context of email transmission.