Use Tor with Firefox to unlock a world of anonymous browsing. This comprehensive guide delves into the intricacies of Tor and Firefox integration, from the basics of anonymity online to advanced configurations. We’ll cover everything from setting up Tor Browser and Firefox to navigating security and privacy concerns, troubleshooting common issues, and exploring practical applications. Get ready to dive deep into the world of secure online activity.
Understanding the fundamental concepts of Tor’s purpose and function is key. Tor, or The Onion Router, is a network that helps you browse the internet anonymously by routing your traffic through various relays. This crucial element makes your online presence harder to track. Firefox, as a web browser, is the primary tool used to access the Tor network. By combining the two, you gain access to an enhanced layer of anonymity and privacy.
This guide is designed to be both informative and easy to follow, empowering you to master the art of secure online browsing.
Introduction to Tor and Firefox
Tor, short for The Onion Router, is a network of volunteer-operated servers designed to enhance online anonymity. It achieves this by routing internet traffic through a series of intermediary servers, obscuring the user’s origin and destination. This layered approach makes it difficult for anyone to trace the user’s online activity back to their original location. This fundamental principle of anonymity is crucial in protecting personal privacy and freedom of expression.Anonymity online, in essence, is the ability to conduct online activities without revealing one’s identity or location to others.
This is important for a variety of reasons, from protecting sensitive information to allowing individuals to express their opinions freely without fear of retribution. Tor, coupled with the right browser, allows users to browse the web with a higher degree of anonymity.
The Role of Firefox in Tor
Firefox, a popular open-source web browser, is well-suited for use with Tor. It provides a secure and reliable platform for users to access the Tor network. Its versatility and wide adoption make it a powerful tool for those seeking anonymity. Furthermore, Firefox has extensions and configurations that allow for seamless integration with Tor, enhancing the browsing experience and maintaining security.
The combination of Firefox and Tor is frequently used for online privacy.
Using Tor with Firefox is a great way to enhance online privacy, but sometimes you just need a little extra something, like checking out the new release of Lightspeed Champion, “Life is Sweet, Nice to Meet You” new release lightspeed champion life is sweet nice to meet you. It’s all about keeping your digital life private, whether you’re browsing the latest gaming releases or just navigating the web securely.
So, remember to keep your digital fortress strong with Tor and Firefox!
History of Tor
Tor’s origins lie in the early 2000s, developed by the US Naval Research Laboratory. It has evolved significantly over the years, with continuous updates and improvements aimed at enhancing security and usability. The project’s open-source nature has fostered a community of developers and users, ensuring its continuous improvement and adaptation to the ever-changing online landscape. Tor’s evolution has been a collaborative effort involving many individuals and groups, making it a strong and robust network.
Benefits and Drawbacks of Using Tor with Firefox
| Benefit | Drawback |
|---|---|
| Enhanced anonymity: Tor’s layered routing and Firefox’s secure architecture effectively mask the user’s identity and location. | Slower browsing speeds: The routing through multiple servers can significantly slow down browsing speed compared to regular internet access. |
| Protection against surveillance: Tor helps to shield users from potential surveillance and tracking by governments, corporations, or other malicious actors. | Limited access to certain websites: Some websites may not function correctly or be accessible when using Tor. This is due to technical limitations or deliberate blocking. |
| Access to censored content: Tor allows users to access content that may be blocked or restricted in their geographical region. | Potential for malicious activity: The anonymity provided by Tor can be exploited for illegal activities such as online crime and harassment. It is crucial to use Tor responsibly. |
| Improved privacy: Tor provides a higher level of privacy for online activities, including financial transactions and personal communications. | Difficulties in troubleshooting: Troubleshooting technical issues can be more complex when using Tor due to the layered nature of the network. |
Setting Up Tor with Firefox
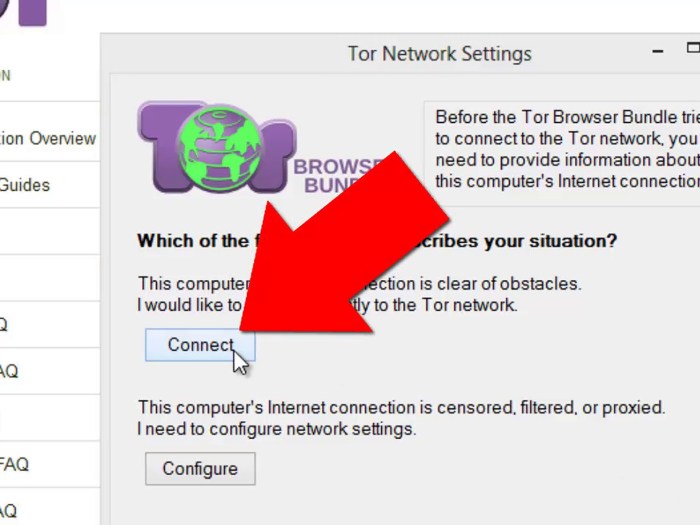
Getting started with Tor involves more than just downloading the browser; it requires understanding the nuances of the network and how to configure your Firefox installation for optimal security. This guide will walk you through the process of installing Tor Browser, configuring Firefox to utilize Tor’s proxy, and understanding the implications of different Tor versions.
Installing Tor Browser
The recommended way to obtain Tor Browser is directly from the official Tor Project website. Downloading from unofficial sources carries potential risks, including malicious code or outdated software. The official website ensures you have the latest security patches and features.
- Download: Visit the official Tor Project website (torproject.org) and navigate to the download section. Choose the appropriate operating system version for your computer (Windows, macOS, Linux). Download the installer file.
- Installation: Run the downloaded installer. Follow the on-screen instructions. Tor Browser installation typically creates a separate folder containing the browser and related files. This isolation is important for security.
Configuring Firefox for Tor
Tor Browser bundles a customized version of Firefox specifically designed for use with the Tor network. This pre-configured setup simplifies the process and reduces the chance of errors. Crucially, this configuration already incorporates the necessary settings for anonymity.
- Launching Tor Browser: Locate the Tor Browser folder. Double-click the executable file to start the Tor Browser. This initiates a Tor connection, routing your traffic through the network. The Tor Browser window will open, and you’ll notice a status bar that will indicate the connection.
- Opening Firefox: Within the Tor Browser, you’ll find a Firefox browser window. This is the instance of Firefox specifically configured to utilize the Tor network.
Tor Versions and Compatibility
Different versions of Tor Browser have varying levels of compatibility with Firefox. The Tor Project releases updated versions regularly, addressing security vulnerabilities and enhancing the anonymity features. Always use the latest stable version to ensure optimal security. Older versions might not have the necessary protections against emerging threats.
- Compatibility: Tor Browser is designed to work seamlessly with the bundled Firefox version. Using older versions of Firefox with Tor might not provide the same level of protection. Always use the most recent version of Tor Browser for the best security.
Configuring Proxy Settings in Firefox for Tor
The Tor Browser automatically configures the necessary proxy settings in Firefox. Manual adjustments are generally not recommended, as incorrect configurations can compromise your anonymity. The bundled configuration in Tor Browser is meticulously designed for security and seamless functionality.
- No Manual Changes: The Tor Browser automatically configures the necessary proxy settings within Firefox. Avoid manually altering proxy settings within the Firefox configuration; this could lead to issues or security risks.
Security and Privacy Aspects
Using Tor with Firefox significantly enhances your online security and privacy, but it’s crucial to understand both the benefits and potential drawbacks. This section delves into the intricacies of Tor’s security features, comparing them with other privacy tools and highlighting potential risks. Awareness of these aspects empowers users to make informed decisions about their online activities.
Using Tor with Firefox is a great way to enhance your online privacy. Thinking about how to make the experience even more unique, you might consider creating a made-up word to describe a specific aspect of your Tor browsing experience, like “cryptonav” for encrypted navigation. Check out this guide on Create a Made Up Word for tips on crafting a new word, and then you can use that made-up word to describe your unique Tor-Firefox setup.
It’s a fun way to personalize your privacy tools!
Security Advantages of Tor with Firefox
Tor’s layered encryption and distributed network architecture offer robust protection against surveillance and censorship. By routing your traffic through multiple servers, Tor masks your IP address, making it difficult for third parties to track your online activities. This anonymity is particularly valuable for journalists, activists, and individuals in countries with restrictive internet policies.
Using Tor with Firefox is a great way to enhance online privacy, but sometimes you might crave a little more control over your digital experience. This can be especially true if you’re interested in exploring the less-traveled corners of the internet, like the fascinating world of bring back afraid dark. Ultimately, using Tor with Firefox allows you to navigate the web with a heightened sense of anonymity and security.
Risks and Vulnerabilities of Tor Usage
While Tor provides a high level of anonymity, it’s not invulnerable. Malicious actors might try to exploit vulnerabilities in Tor’s software or network. Using Tor with outdated versions of Firefox or Tor itself can create security weaknesses. Compromised intermediary nodes (Tor relays) are another potential threat, though their occurrence is comparatively rare. Users must exercise caution and update their software regularly to mitigate these risks.
How Tor Protects User Privacy
Tor protects user privacy by obscuring the origin and destination of their internet traffic. The network’s distributed nature and encryption layers effectively hide your online activities from surveillance. This anonymity is particularly crucial for protecting sensitive information and maintaining personal privacy.
Comparison of Tor’s Security Features with Other Privacy-Enhancing Technologies
Tor’s distributed architecture distinguishes it from other privacy-enhancing technologies like VPNs. While VPNs typically encrypt traffic through a single server, Tor’s layered approach provides a greater degree of anonymity. However, VPNs are often more user-friendly and faster, making them attractive alternatives in certain scenarios. Each technology has its strengths and weaknesses.
Potential Risks of Using Tor and Firefox with Examples
Using Tor with Firefox might introduce risks. For instance, downloading files from untrusted sources over Tor could expose your system to malware. Furthermore, relying solely on Tor for online banking or financial transactions might not be entirely safe. Malicious actors could try to intercept or manipulate your communication, especially in poorly configured setups. Carefully vetting websites and exercising caution are crucial for mitigating these potential risks.
Table of Security Measures for Tor with Firefox
| Security Measure | Description | Importance |
|---|---|---|
| Regular Software Updates | Keeping both Tor and Firefox up-to-date patches security vulnerabilities. | Critical for maintaining protection against exploits. |
| Using a Strong Password Manager | Managing passwords securely across different accounts. | Reduces risk of compromise if one account is breached. |
| Avoiding Suspicious Links/Downloads | Be cautious when clicking links or downloading files from unknown sources. | Prevents exposure to malware or phishing attacks. |
| Employing a Separate Tor Browser Profile | Creating a dedicated browser profile for Tor activities. | Reduces the risk of data leakage between Tor and non-Tor browsing. |
| Using a Secure Network | Using a secure network connection whenever possible, especially for sensitive transactions. | Mitigates risks of man-in-the-middle attacks. |
Practical Applications and Use Cases
Tor with Firefox offers a powerful combination for enhanced online privacy and security. Beyond the obvious use for accessing censored content, its applications extend to a wide range of legitimate and crucial scenarios. This section delves into various practical use cases and demonstrates the benefits of leveraging this combination over standard browsers.
Situations Benefiting from Tor with Firefox
Tor with Firefox is a valuable tool in situations where anonymity and privacy are paramount. It provides a crucial layer of protection against surveillance and tracking, making it a preferred choice over standard browsers in specific contexts. For example, journalists investigating sensitive topics or activists advocating for social change often utilize Tor for secure communication and information gathering.
Furthermore, individuals in countries with strict internet censorship rely on Tor to access information otherwise blocked.
Accessing Blocked Websites
Tor circumvents geographical restrictions and censorship by routing your traffic through a network of volunteer relays. This makes it possible to access websites and online services that may be blocked or restricted in certain regions. This is particularly useful for individuals in countries with strict internet censorship, enabling them to access news, information, and communication tools that might be otherwise unavailable.
For example, a user in China could use Tor to access a news website blocked by the Great Firewall.
Anonymous Online Activities
Tor with Firefox facilitates anonymous online activities, protecting user identities and preventing tracking by websites and third parties. This is particularly important for sensitive activities like online banking, participating in forums with controversial opinions, or engaging in online activism without revealing personal information. For example, an individual participating in a politically charged online forum can do so without their IP address being linked to their identity.
Legitimate Use Cases
Tor with Firefox is not solely for illicit activities. Its legitimate applications are numerous and crucial for individuals and organizations. For example, researchers can use Tor for anonymous data collection and analysis without revealing their identities. Furthermore, individuals who need to protect their privacy while using online services, such as financial transactions or sensitive communications, can leverage Tor.
These examples illustrate the wide range of legitimate uses for this technology.
Comparison Table: Tor with Firefox vs. Standard Browsers
| Use Case | Tor with Firefox | Standard Browser |
|---|---|---|
| Accessing blocked websites | Effective in bypassing geographical restrictions and censorship. | Limited by regional restrictions and censorship. |
| Anonymous online activities | Protects user identity and prevents tracking. | Vulnerable to tracking and surveillance. |
| Journalistic investigations | Ensures anonymity and security during sensitive research. | May compromise anonymity during investigations. |
| Online activism | Provides a secure platform for expressing opinions and participating in online advocacy. | May reveal personal information during online activism. |
| Protecting privacy during sensitive transactions | Hides IP address and location during online financial transactions. | Potentially reveals IP address and location during online transactions. |
Troubleshooting and Common Issues: Use Tor With Firefox
Navigating the digital landscape anonymously with Tor and Firefox can sometimes present challenges. This section delves into common problems users face, providing solutions and insights to ensure a smooth and effective experience. Understanding these potential pitfalls is crucial for a secure and efficient online journey.Troubleshooting Tor and Firefox interactions often involves recognizing patterns and applying targeted fixes. A systematic approach, Artikeld below, helps users identify and resolve issues, optimizing their anonymity and privacy online.
Common Connection Problems
Connection issues are a frequent concern when using Tor. These problems can stem from various factors, including network instability, Tor network congestion, or configuration errors. Understanding the root causes is essential for effective troubleshooting.
- Slow or intermittent connections: Network congestion on the Tor network can lead to slow or intermittent connections. Try waiting a few minutes or refreshing the page, as temporary network issues may resolve themselves.
- Connection refused errors: A “connection refused” error indicates that the Tor server is unable to establish a connection. Check your internet connection, ensure the Tor browser is up-to-date, and verify that the Tor network is functioning correctly.
- Proxy server not found: If the proxy server is not found, it means that the Tor browser isn’t correctly configured to connect to the Tor network. Double-check the Tor browser settings to ensure the proxy server settings are accurate.
Performance Issues
Performance bottlenecks can arise from various sources, affecting the speed and responsiveness of Tor-based browsing. A thorough understanding of potential causes is critical for finding the right solutions.
- Slow page loading times: Tor’s layered routing system inherently adds latency to connections. Use a faster internet connection or consider optimizing the websites you visit for quicker loading times.
- High CPU usage: If the Tor browser is consuming excessive CPU resources, it could indicate a problem with the browser’s configuration or a resource-intensive website. Close unnecessary tabs or applications, and ensure the browser has adequate system resources.
- Memory leaks: Memory leaks in the Tor browser can cause performance issues. Occasionally, restarting the browser may resolve these issues.
Overcoming Limitations
While Tor provides robust anonymity, it’s not without limitations. Understanding these constraints is vital for effectively leveraging its capabilities.
- Tor’s speed limitations: Tor’s layered routing architecture can lead to slower browsing speeds compared to standard connections. This is a known characteristic of the network and not necessarily a cause for concern.
- Compatibility issues with specific websites: Some websites might not be compatible with Tor’s proxy system. In these cases, using alternative browsing methods or exploring workarounds might be necessary.
- Potential for blocking: Websites may detect and block Tor users. Consider using a VPN in conjunction with Tor for enhanced anonymity.
Troubleshooting Guide, Use Tor with Firefox
- Verify internet connection: Ensure your internet connection is stable and functioning correctly.
- Check Tor browser updates: Make sure your Tor browser is up-to-date to benefit from bug fixes and performance improvements.
- Restart the Tor browser: A simple restart can often resolve temporary glitches.
- Clear browser cache and cookies: Removing cached data can sometimes address performance issues.
- Adjust proxy settings: Verify that the proxy settings in the Tor browser are correctly configured.
- Contact Tor support: If the issue persists, consult Tor’s support channels for assistance.
Common Errors and Solutions
| Error | Solution |
|---|---|
| Connection refused | Verify internet connection, check Tor network status, and restart the browser. |
| Proxy server not found | Ensure the Tor browser’s proxy settings are accurate. |
| Slow page loading | Optimize website loading, use a faster internet connection. |
| High CPU usage | Close unnecessary tabs, ensure adequate system resources. |
Advanced Configurations and Features
Diving deeper into Tor’s capabilities reveals a world of customization options beyond the basic setup. This section explores advanced configurations for Firefox, enabling users to tailor Tor’s behavior to specific needs and enhance security. Understanding these advanced settings empowers users to optimize their privacy and anonymity.
Customizing Tor Settings
Advanced Tor configurations allow for precise control over how the browser interacts with the network. This can range from selecting specific Tor circuits to configuring the use of bridges, ultimately increasing anonymity and bypassing potential censorship. By understanding and leveraging these options, users can further enhance their privacy.
Circuit Selection
Tor’s circuit selection mechanism plays a critical role in anonymity. Tor randomly chooses a path through a series of relays to conceal the user’s origin and destination. Understanding the intricacies of circuit selection enables users to mitigate potential vulnerabilities and choose paths that align with their security preferences. The specific circuit chosen can influence the user’s perceived latency and speed.
Carefully configuring circuit selection can be important for optimizing performance.
Tor Bridges
Tor bridges provide alternative entry points to the Tor network. They are often used to circumvent censorship or network restrictions, ensuring continued access to the Tor network. This feature allows users to bypass restrictions and access content that may be blocked in their geographical location. These bridges are often maintained by volunteers.
Understanding Tor’s Circuit Details
Examining the specifics of Tor’s circuit is crucial for understanding its operational mechanics and the impact on security. Understanding how Tor selects relays, and the number of relays involved, provides insight into the potential for identification and vulnerability. Knowing the relay locations and characteristics allows for a more informed assessment of security. A detailed understanding of the circuit path allows for potential mitigation of vulnerabilities.
Setting Up Tor Relays
Setting up a Tor relay involves participating in the Tor network by operating a relay node. This requires technical expertise and resources. The process involves installing and configuring the Tor software on a dedicated server. Running a relay node contributes to the overall resilience and functionality of the Tor network, but requires careful configuration.
Advanced Tor Features
| Feature | Functionality |
|---|---|
| Circuit Selection | Allows users to customize the path through the Tor network. |
| Tor Bridges | Provide alternative entry points to the Tor network, bypassing potential restrictions. |
| Relay Configuration | Enables users to run their own Tor relay node, contributing to the network. |
| Customizable Settings | Offers detailed control over various Tor aspects, including circuit selection, latency, and bandwidth usage. |
Alternatives and Comparisons
Tor with Firefox, while a powerful anonymity tool, isn’t the only option. Understanding its strengths and weaknesses in comparison to other methods is crucial for choosing the right solution for your specific needs. This section explores alternative anonymization tools and analyzes their respective advantages and disadvantages.Choosing an anonymization tool depends on the specific privacy and security requirements. Factors like the level of anonymity needed, the technical expertise of the user, and the intended use cases play significant roles in the decision-making process.
A thorough comparison is essential for making an informed choice.
Alternative Anonymity Tools
Several alternative anonymity tools cater to different needs and technical proficiencies. Their features and limitations vary, making a comparison crucial for informed decision-making.
- VPN (Virtual Private Network): VPNs encrypt internet traffic and route it through a server in a different location. This masks the user’s IP address, offering a basic level of anonymity. VPNs are relatively easy to set up and use, but their anonymity level is dependent on the VPN provider’s policies and security practices. Some VPNs might log user activity, which compromises anonymity.
- Proxy Servers: Proxy servers act as intermediaries between the user’s device and the internet. Similar to VPNs, they can mask the user’s IP address, but they often offer less robust encryption and security features. Proxy servers might be more limited in functionality than VPNs, but are generally easier to configure and use.
- I2P (Invisible Internet Project): I2P is a decentralized network similar to Tor, aiming to provide a more robust and resilient alternative. It features a distributed network structure, making it potentially more resistant to censorship and surveillance. However, I2P can be more complex to set up and use compared to Tor and VPNs.
- Other Privacy-focused Browsers: Browsers like Brave and Tor Browser are built with privacy in mind, implementing features like anti-tracking and ad blocking. While they enhance privacy within the browser, they don’t offer the same level of end-to-end anonymity as Tor, which masks traffic throughout the network.
Advantages and Disadvantages
Understanding the strengths and weaknesses of each anonymity tool is crucial for making the right choice. Here’s a brief overview:
- Tor with Firefox: Offers strong anonymity through its layered network. It is robust, but can be slower than other methods due to the multiple hops involved in the network. The user experience can sometimes be more complex than a straightforward VPN.
- VPNs: Generally faster than Tor due to a single connection path. Ease of use and accessibility are significant advantages, but the anonymity depends on the VPN provider’s practices. Potential risks exist if the provider logs user data or compromises security.
- Proxy Servers: Often faster than Tor, providing a simple way to mask the IP address. However, they may lack robust encryption, potentially exposing the user to security vulnerabilities.
- I2P: Offers a decentralized approach with potential benefits in terms of censorship resistance. The setup and usage can be more complex than other alternatives. The network’s size and activity level can influence performance.
- Privacy-focused Browsers: Enhance privacy within the browser by blocking trackers and ads, but do not provide the same level of anonymity as Tor, which masks traffic across the entire network.
Comparative Analysis
The following table summarizes the key characteristics of different anonymity tools.
| Feature | Tor with Firefox | VPN | Proxy Server | I2P | Privacy-focused Browsers |
|---|---|---|---|---|---|
| Anonymity | High | Medium-High (depends on provider) | Low-Medium | High | Low |
| Speed | Slow | Fast | Fast | Variable | Medium |
| Complexity | Medium | Low | Low | High | Low |
| Security | High | High (depends on provider) | Low | High | Medium |
Situations Favoring Alternatives
The best anonymity tool depends on the specific use case. Consider the following situations:
- Streaming content: VPNs are a preferable choice due to their speed and ability to bypass geo-restrictions.
- Everyday web browsing: A VPN or a privacy-focused browser might suffice for most users.
- High-risk activities requiring strong anonymity: Tor with Firefox is the most appropriate choice.
- Circumventing censorship: I2P might be preferred due to its decentralized nature.
Limitations of Tor with Firefox
Tor with Firefox, while robust, has limitations compared to other tools:
- Speed: The layered network structure can significantly impact browsing speed.
- Complexity: Setup and usage can be more complex compared to VPNs or proxy servers.
- Performance: High traffic volumes can result in slower performance.
Last Word
In conclusion, using Tor with Firefox empowers you with a robust toolkit for online privacy and security. From basic setup to advanced configurations, this guide provides a thorough understanding of the process. Remember, while Tor enhances anonymity, it’s not a foolproof solution. Responsible usage and awareness of potential risks are crucial. So, equip yourself with this knowledge and embark on your anonymous online journey with confidence.