Log in to Spotify – a seemingly simple task, yet a complex process lies beneath the surface. This exploration delves into the intricacies of the Spotify login, from the user’s perspective to the technical underpinnings, and everything in between. We’ll examine the user experience, security protocols, technical implementation, error handling, and accessibility considerations.
Understanding the Spotify login process is crucial for both users and developers. This in-depth look will dissect each stage, highlighting the challenges and best practices for creating a smooth, secure, and accessible login experience. From the initial page load to successful authentication, we’ll cover it all.
User Experience (UX) of the Log-in Process
Logging into Spotify, a ubiquitous music streaming service, is a crucial part of the user experience. A smooth and intuitive login process is essential for user satisfaction and retention. This section delves into the typical user journey, common pain points, and compares Spotify’s approach with competitors.The user’s interaction with the login system is the first impression of the platform.
A well-designed system ensures ease of use and minimizes frustration. This approach allows users to quickly access their desired content, reducing friction and improving overall satisfaction.
Typical User Journey
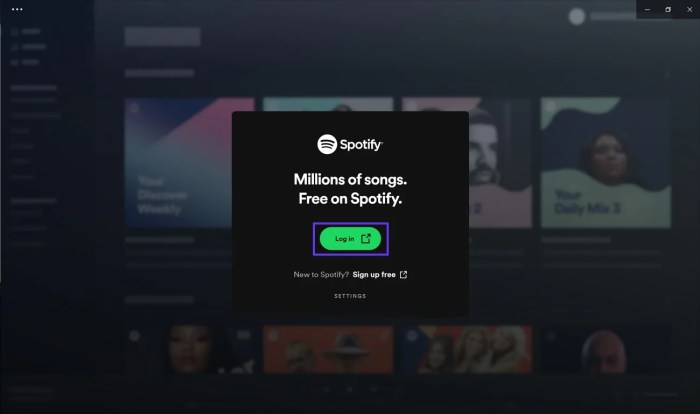
The typical user journey begins with the user navigating to the Spotify website or app. The login screen appears, prompting the user to enter their credentials. This typically involves a username or email address field and a password field. After entering the credentials, the user clicks a “Log In” button. Spotify then validates the credentials against its database.
Upon successful authentication, the user is redirected to their personalized dashboard or the page they were previously on. If the credentials are incorrect, an error message is displayed, prompting the user to re-enter the credentials.
Steps in the Login Process
- The user initiates the login process by opening the Spotify application or website.
- The login screen is displayed, presenting fields for username/email and password.
- The user inputs their credentials.
- The user clicks the “Log In” button.
- Spotify validates the entered credentials against its user database.
- If authentication is successful, the user is redirected to their intended destination (e.g., their profile page or the page they were previously on). If unsuccessful, an error message is displayed.
Common Pain Points
Users may encounter various pain points during the login process. Forgotten passwords are a common issue, leading to frustration and potentially lost accounts. Inconsistent or overly complex login flows can also be problematic. Users might experience slow loading times, which negatively impacts their experience. Technical glitches or intermittent connectivity problems can further contribute to frustrating login experiences.
Finally, a lack of clear error messages can leave users confused and unable to resolve login issues.
User Flow Diagram
[A user flow diagram would visually represent the steps Artikeld above. It would depict the user’s actions, the system’s responses, and the transitions between different screens. The diagram would clearly illustrate the flow from initial page load to successful authentication, highlighting any potential points of failure.]
Comparison with Competitors
Spotify’s login process generally compares favorably to competitors like Apple Music or YouTube Music. While each platform has its unique features and implementations, Spotify’s approach typically prioritizes user-friendliness and a streamlined process. However, some competitors may have more integrated login options through existing accounts, such as using Google or Facebook accounts. The key differentiator lies in the user experience provided by each platform.
Spotify generally aims for simplicity, while other services may offer more options, potentially complicating the login process.
Security Considerations of the Log-in
The security of user accounts is paramount for any online platform, and Spotify is no exception. A robust log-in system is critical to protecting user data and maintaining trust. This discussion will delve into the security measures Spotify employs to safeguard user accounts, highlighting the importance of strong passwords and multi-factor authentication. It will also Artikel potential threats and best practices for building a secure log-in system.A secure log-in process is not just about preventing immediate unauthorized access; it also safeguards against more sophisticated attacks and protects sensitive user data.
This involves understanding the types of threats that can be targeted at the log-in process, from simple password guessing to more complex techniques like phishing and man-in-the-middle attacks. Effective security measures are essential to maintain user confidence and prevent financial or reputational damage.
Spotify’s Security Measures
Spotify utilizes a multi-layered approach to protect user accounts during the log-in process. These measures are designed to deter unauthorized access and ensure the integrity of user data. The platform employs encryption protocols to safeguard the transmission of login credentials, and regular security audits are conducted to identify and address vulnerabilities.
Importance of Strong Passwords
Creating strong passwords is a fundamental step in enhancing account security. A strong password is complex, incorporating a combination of uppercase and lowercase letters, numbers, and symbols. The length of the password also plays a crucial role, as longer passwords are more resistant to brute-force attacks. Avoid using easily guessable information, such as birthdates, names, or common words.
Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security to the log-in process. 2FA requires users to provide two forms of verification, such as a password and a code from a mobile device or authenticator app. This significantly reduces the risk of unauthorized access even if a password is compromised. Spotify’s 2FA implementation enhances security, making it more difficult for attackers to gain access to user accounts.
Security Threats to the Log-in Process
Various security threats can target the log-in process. Phishing attacks, where malicious actors attempt to trick users into revealing their credentials, are a common concern. Man-in-the-middle attacks intercept communication between the user and the platform, potentially compromising login information. Brute-force attacks attempt to guess passwords through trial and error. Malicious software or malware can also be used to steal login credentials.
These threats underscore the need for robust security measures and user vigilance.
Just logged in to Spotify, ready to blast some tunes. Speaking of music, did you know Julian Casablancas is playing his first solo show in Tokyo? It’s going to be epic! This show looks amazing, and I’m already planning my Spotify playlist for the next few days. Now, back to jamming!
Creating a Secure Log-in System
Implementing a secure log-in system involves a comprehensive approach. Encryption plays a vital role in protecting sensitive data during transmission. Regular security audits and penetration testing are essential to identify and address potential vulnerabilities. Strong passwords and 2FA are critical security measures. Educating users about security best practices and threats, including phishing awareness, is vital for a robust security strategy.
User awareness and proper security measures are integral to preventing attacks.
Technical Aspects of the Log-in
The Spotify login process, crucial for user access and service provision, relies on a robust technical infrastructure. Understanding the underlying technologies ensures a smooth and secure experience. This section details the technical components and considerations involved.The Spotify login system employs a layered architecture, combining multiple technologies to manage user authentication and authorization securely. This approach ensures scalability and resilience, allowing the platform to handle a large volume of concurrent login requests while maintaining security.
Authentication Infrastructure
The authentication process is the core of the login system. It verifies the user’s identity before granting access. Spotify employs a sophisticated architecture encompassing multiple components working in concert. The system needs to handle various authentication methods while maintaining security and user experience.
Authentication Methods Supported
Spotify supports various authentication methods, each with its unique strengths and weaknesses. This flexibility accommodates different user preferences and security needs.
- Password-based authentication: This traditional method utilizes a username and password combination. It’s a widely used approach, but susceptible to security breaches if passwords are not managed securely.
- OAuth 2.0: This authorization framework allows third-party applications to access user data without requiring them to store user credentials. This enhances security and user privacy.
- Multi-factor authentication (MFA): Spotify integrates MFA, requiring users to provide additional verification steps beyond a password, such as a one-time code sent to their phone or an authentication app. This substantially strengthens security against unauthorized access.
Authorization Mechanism
Authorization determines what resources a user can access after successful authentication. This process controls access to Spotify’s extensive library and features.Spotify utilizes role-based access control (RBAC). Different user roles (e.g., free user, premium user) have varying access privileges. This ensures that only authorized users can access specific features or content.
The Log-in Process Summary
The Spotify login process involves several stages, each designed to ensure security and efficiency.
- User Input: The user enters their credentials (username/password, or chosen authentication method).
- Authentication Verification: Spotify verifies the user’s identity using the chosen authentication method. This involves hashing and comparing passwords for security.
- Authorization Check: The system determines the user’s access privileges based on their account type and role.
- Session Management: A secure session is established, granting the user access to the platform. This session is typically managed with tokens to maintain security and minimize user input for subsequent actions.
Technical Challenges and Solutions
Several technical challenges can arise during the login process. Addressing these challenges is crucial for a seamless user experience and platform stability.
- Scalability: Handling a large number of concurrent login requests requires robust infrastructure. Spotify likely uses load balancers and distributed databases to manage high traffic volumes.
- Security Breaches: Protecting user credentials from unauthorized access is paramount. Implementing strong encryption, secure hashing algorithms, and regular security audits mitigates risks.
- Integration with Third-Party Services: Integrating with external services, such as OAuth providers, requires careful management to ensure compatibility and security. Strict adherence to security standards for external services is essential.
Error Handling and User Support
A robust log-in process relies heavily on effective error handling and user support. Users expect a smooth and reliable experience, and a well-designed system for addressing errors is crucial for maintaining user satisfaction and trust. This section details how Spotify tackles these challenges, ensuring a positive user experience even when unexpected issues arise.
Spotify’s Error Handling Mechanisms
Spotify employs a multi-layered approach to error handling during the log-in process. This involves identifying the source of the problem, providing relevant error messages, and guiding users toward resolution. Different error scenarios trigger different responses, ranging from simple prompts to more complex interactive troubleshooting steps.
Error Messages and Their Context
Spotify displays clear and concise error messages, tailored to the specific problem encountered. These messages typically fall into categories such as network issues, account problems, or authentication failures. Examples include:
- Network Error: “Unable to connect to Spotify servers. Please check your internet connection and try again.” This message clearly identifies the problem and suggests a common solution.
- Incorrect Credentials: “Incorrect username or password. Please try again.” This is a straightforward error message that directly guides the user.
- Account Suspension: “Your Spotify account has been suspended. Please contact support for assistance.” This message informs the user of a more serious issue and directs them to appropriate channels.
The clarity and specificity of these messages are key to minimizing user frustration and promoting efficient troubleshooting.
Just logged in to Spotify, and you know what? There’s a brand new Grizzly Bear track featuring Michael McDonald, which is a delightful surprise. Check out the new single michael mcdonald sings on new grizzly bear single – it’s definitely worth a listen! Now, back to exploring the rest of my Spotify playlist.
Methods of Informing Users About Log-in Status
Spotify uses various methods to keep users informed about the log-in process, providing feedback at different stages. These include:
- Progress Indicators: Loading spinners and visual cues during authentication stages provide users with immediate feedback that the system is working.
- Interactive Feedback: Error messages often include specific instructions on how to proceed or provide context on the issue encountered, guiding users toward resolution.
- Status Bar Updates: Updates in the status bar or pop-up messages offer concise summaries of the log-in status.
Robust Error Handling System Design
A robust error handling system goes beyond simply displaying error messages. It involves comprehensive logging, efficient categorization of errors, and automatic escalation procedures when necessary.
- Logging: Comprehensive logs of every interaction during the log-in process help in identifying patterns, tracking down recurring problems, and improving the system’s resilience.
- Error Categorization: Classifying errors into categories (e.g., network, authentication, account) allows for focused analysis and prioritization of fixes.
- Automated Escalation: A system that automatically escalates critical errors to support teams ensures timely resolution and prevents prolonged user frustration.
Troubleshooting Common Log-in Problems
A dedicated troubleshooting guide on Spotify’s website or help center can be invaluable for users encountering common log-in problems. This guide should include clear instructions and steps for users to resolve issues independently.
- Clear Steps: Provide step-by-step instructions on how to resolve common issues like password resets, account recovery, or network connectivity problems.
- Comprehensive Examples: Illustrate various scenarios with specific examples of how users can resolve the issues. For instance, explain how to troubleshoot proxy server issues or specific firewall configurations.
- User-Friendly Language: Use clear and simple language to guide users through the troubleshooting process, avoiding technical jargon.
Accessibility and Inclusivity of the Log-in: Log In To Spotify
Spotify’s commitment to accessibility extends beyond just a good user experience; it’s a fundamental principle built into their entire platform. A seamless and usable log-in process is crucial for everyone, especially those with disabilities. This section explores how Spotify ensures accessibility, Artikels compliance, identifies potential issues, and emphasizes the importance of clear communication during the login.Spotify’s commitment to accessibility translates to a more inclusive and equitable platform for all users.
The log-in process is designed with inclusivity in mind, aiming to provide equal opportunities for all users to enjoy Spotify’s services, regardless of their abilities.
Compliance with Accessibility Standards
Spotify adheres to widely recognized accessibility standards like WCAG (Web Content Accessibility Guidelines). These guidelines provide a framework for creating websites and applications that are usable by people with a wide range of disabilities. Specific checkpoints address critical areas like perceivable content, operable controls, understandable content, and robust content. The standards cover everything from sufficient color contrast to alternative text for images and keyboard navigation.
Potential Accessibility Issues with the Spotify Log-in
While Spotify strives for a fully accessible log-in, potential issues can arise. One potential area is insufficient color contrast between text and background colors, especially for users with low vision or color blindness. Another issue might be the reliance on complex animations or transitions that are not easily navigable for users with cognitive disabilities or seizure disorders. Also, the log-in process might not be adequately optimized for screen readers, impacting users who rely on these technologies.
Finally, insufficient keyboard navigation within the log-in forms could pose challenges for users who cannot use a mouse or touchpad.
Importance of Clear and Concise Language
Clear and concise language is essential for an inclusive log-in process. Ambiguous or overly technical language can exclude users who have cognitive disabilities or language barriers. Using simple, direct language that avoids jargon or technical terms is crucial. Providing multiple language options also caters to users who may have different language preferences or needs.
Best Practices for Creating an Inclusive Log-in Experience
Implementing best practices is paramount to achieving an inclusive log-in experience. A robust accessibility strategy encompasses multiple aspects:
- Comprehensive User Testing: Regularly testing the log-in process with users who have various disabilities is essential to identify and address any usability issues.
- Utilizing Assistive Technologies: Thoroughly testing the log-in process with assistive technologies like screen readers and keyboard navigation is crucial to ensuring seamless operation for users with disabilities.
- Ensuring Adequate Color Contrast: Using appropriate color contrast ratios between text and backgrounds is critical for users with low vision or color blindness. Tools are available to check and adjust color palettes.
- Avoiding Complex Animations and Transitions: Limiting or providing alternative mechanisms for complex animations and transitions is crucial to avoid triggering seizures or other issues for users with sensory sensitivities. A user-friendly approach is crucial.
- Providing Clear Error Messages: Detailed and clear error messages, presented in a manner that is accessible to users employing assistive technologies, is paramount.
Design and Visual Aspects of the Log-in Page
The visual design of a login page is crucial for a positive user experience. A well-designed login page should be intuitive, aesthetically pleasing, and secure. It should guide users effortlessly through the process while reassuring them about the safety of their information. A strong visual identity is critical for building brand recognition and fostering trust.The design of the login page directly impacts user engagement and ultimately affects the success of the login process.
Careful consideration of color schemes, typography, layout, and visual cues contributes to a seamless and trustworthy experience. The aesthetic elements and layout must be consistent with the overall brand identity of Spotify.
Color Scheme
A well-chosen color palette sets the tone and mood of the login page. Spotify’s branding often uses a vibrant, yet approachable color scheme. The login page should use a color scheme that aligns with the existing Spotify color palette, creating a cohesive and recognizable visual experience for the user. A balanced approach that uses primary colors and accents that are not overwhelming or distracting is ideal.
This palette should also be adaptable across various devices and screen sizes to maintain visual consistency.
Typography
Font selection plays a vital role in establishing brand identity and readability. Clear, legible fonts are essential for easy comprehension. The chosen font should complement the overall design and branding. Appropriate font sizes, styles, and line spacing are critical for optimal readability, especially for users with visual impairments. A consistent font hierarchy is important for differentiating elements like headings, subheadings, and input fields.
Layout and Visual Elements
The layout of the login page should be organized and easy to navigate. Key elements, such as the logo, input fields, and buttons, should be strategically positioned for optimal usability. Whitespace should be strategically used to create visual separation and improve readability. Visual cues, such as progress indicators or loading animations, are vital for informing users about the status of the login process.
These cues can be subtle animations or visual indicators to show the user the system is working.
Visual Cues and Feedback
Visual cues are important to guide users through the login process. Clear visual feedback, such as highlighting the active input field or changing the button’s appearance after clicking, is crucial for user understanding and reassurance. Error messages should be presented clearly and concisely with visual indicators, such as a red border around the input field, to draw attention to any problems.
Positive feedback, like a subtle animation or a change in color, after successful login, reinforces a positive user experience.
Responsive Design
A responsive design is essential for ensuring a seamless experience across different devices. The layout and visual elements should adapt to various screen sizes and orientations.
| Device | Font Size | Layout | Visual Cues |
|---|---|---|---|
| Desktop | Default | Full-width elements | Large, prominent buttons |
| Tablet | Slightly reduced | Adjusted layout for optimal viewing | Clear visual cues, maintaining button size |
| Mobile | Reduced for optimal readability | Simplified layout | Smaller, but still clear visual cues |
User Interface (UI) Best Practices for Log-in
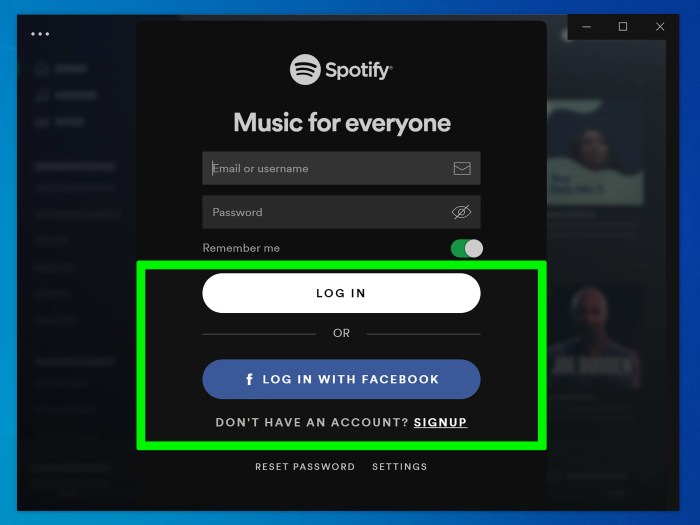
Crafting a seamless and user-friendly login experience is crucial for any application. A well-designed login form not only streamlines the process but also builds user trust and encourages repeat engagement. This section delves into essential UI best practices, focusing on clear labeling, consistent design, intuitive navigation, and valuable user feedback.A robust login UI is a cornerstone of a positive user experience.
Clear and concise instructions, coupled with aesthetically pleasing visuals, significantly impact user satisfaction. It’s about more than just functionality; it’s about creating an experience that users find both easy and enjoyable.
Clear Labeling and Input Fields
Clear labeling is paramount for a smooth login process. Users should immediately understand the purpose of each field without needing to resort to guesswork or extensive reading. Descriptive labels, such as “Email Address” or “Password,” are essential for user comprehension. Avoid ambiguous or overly technical terminology.
- Use clear and concise labels for all input fields. Avoid abbreviations or overly technical terms. For instance, instead of “UsrNm,” use “Email Address.”
- Provide visual cues to indicate the type of input required. For example, an asterisk (*) beside a required field helps users identify mandatory inputs. Icons or visual cues related to the type of input are beneficial. A padlock icon for password fields, or a mail icon for email addresses.
- Consider using placeholder text within the input fields. This helps users understand the expected format and provides a visual guide, like “Enter your email address.”
Consistent Design and Visual Hierarchy, Log in to Spotify
Maintaining a consistent design throughout the login form and the application is critical for user recognition and ease of use. Consistent visual elements, like font styles and color schemes, create a sense of familiarity and trust. A clear visual hierarchy guides the user’s eye to essential elements, such as the submit button.
- Employ a consistent color scheme and typography across the application. This creates a sense of cohesion and familiarity for the user.
- Use a clear visual hierarchy to guide the user’s attention to crucial elements. Important elements, such as the submit button, should be prominently displayed.
- Maintain a consistent layout for all input fields and elements. This ensures that users can easily find the information they need.
Intuitive Navigation and Feedback
Intuitive navigation is key to a positive user experience. The login process should be straightforward, allowing users to easily locate the necessary fields and submit their credentials. Effective feedback mechanisms are equally important. Providing immediate feedback on input validation, such as error messages or confirmation messages, reduces user frustration.
- Implement clear and concise error messages. These should provide specific feedback about the nature of the error and how to correct it, such as “Please enter a valid email address.”
- Use visual cues, like highlighting or animation, to indicate the status of form elements. This enhances user interaction and provides immediate feedback.
- Employ loading indicators to keep users informed during form submissions. A simple loading animation or a message indicating the process will help maintain user trust.
Examples of Good and Bad UI Designs
| Good Design | Bad Design |
|---|---|
| A well-structured login form with clear labels, consistent styling, and a visually appealing layout. The input fields are easily identifiable, and the overall design enhances the user experience. | A cluttered login form with confusing labels, inconsistent styling, and a visually unappealing layout. The input fields are not easily identifiable, and the overall design hinders the user experience. |
- A good design prioritizes clear and concise communication, reducing the cognitive load on the user. The visual hierarchy clearly guides the user’s attention to important elements, while a bad design is cluttered and disorienting.
User Feedback in the Login Process
User feedback is critical for iterative improvement in the design of a login form. Collecting and analyzing user feedback can reveal pain points and areas for improvement. This data helps to refine the design, leading to a more intuitive and user-friendly experience.
- Collect feedback through various channels, such as user surveys, feedback forms, or direct interaction with users during testing.
- Analyze the feedback to identify recurring issues and areas for improvement in the login process.
- Use the data to refine the design, leading to a more intuitive and user-friendly login form.
Log-in Process Evolution and Trends
The evolution of log-in processes mirrors the broader technological advancements of our time. From simple usernames and passwords to multi-factor authentication and biometric identification, the methods we use to access online services have become increasingly sophisticated and secure. This evolution is driven by the need for enhanced user experience, heightened security, and adaptation to emerging technologies.The log-in process, once a straightforward task, has become a complex interplay of security, usability, and technological innovation.
The design and implementation of these systems directly impact user trust and the overall health of online platforms. Understanding this evolution provides valuable insight into future trends and best practices.
Evolution of Log-in Methods
Early online systems often relied on simple username and password combinations. Security was often rudimentary, and user experience was not a primary consideration. This basic approach was sufficient for a limited number of users, but as the internet expanded and online services became more prevalent, more sophisticated log-in mechanisms were required.
Logging in to Spotify is usually pretty straightforward, but sometimes I find myself agonizing over the password. It’s oddly similar to the jitters I get when meeting a new guy, like the ones explored in this insightful article on Why Do You Feel Nervous Around a Guy. Maybe it’s just the anticipation of the music, or maybe it’s a deeper psychological issue?
Either way, once I get past the initial anxiety, I’m usually able to find my favorite tunes and chill out. Back to Spotify!
Comparison of Log-in Methods Across Platforms
Different platforms employ varying log-in methods, often reflecting their specific needs and user base. For example, social media platforms frequently utilize existing social media accounts for streamlined sign-up and log-in. E-commerce sites prioritize secure payment methods and often integrate with third-party payment gateways, which necessitates robust authentication procedures. Financial institutions, due to their sensitivity to fraud, often employ more stringent security measures like multi-factor authentication.
Current Trends and Emerging Technologies
Several current trends and emerging technologies are reshaping log-in processes. Passwordless authentication, employing methods like biometrics and one-time passwords, is gaining significant traction. Additionally, the use of device fingerprinting and contextual authentication adds layers of security and usability. The rise of the Web3 and decentralized applications introduces new challenges and opportunities for log-in processes, requiring novel approaches to user identity management and security.
Timeline of Key Milestones in Log-in Process Evolution
- 1990s: Emergence of the internet and basic username/password systems. Security was often a secondary concern.
- Early 2000s: Introduction of more complex password policies and the concept of strong passwords. Increased awareness of security vulnerabilities.
- Mid-2000s: Rise of social media platforms and the integration of social logins. This simplified the process for users but raised concerns about data privacy.
- 2010s: Growing use of multi-factor authentication (MFA). MFA adds an extra layer of security by requiring multiple verification steps, like a code sent to a mobile device.
- Present: Passwordless authentication and biometric log-ins. Biometric log-ins like fingerprint scanning and facial recognition are becoming more common.
Innovative Approaches to the Log-in Process
Innovative approaches to the log-in process are driven by the need for enhanced security and user experience. Some notable examples include:
- Passwordless authentication: Eliminating the need for passwords entirely, relying on other methods like biometrics or one-time codes. This simplifies the process and enhances security.
- Contextual authentication: Adapting the authentication process based on the user’s current environment, like location or device. This helps reduce fraud attempts.
- Integration with hardware security modules (HSMs): Utilizing hardware security modules to store and manage cryptographic keys, providing an extra layer of security.
Alternative Log-in Methods
Spotify’s login process can be significantly enhanced by offering alternative methods beyond traditional username/password combinations. These alternatives improve user experience, increase security, and streamline the process for various user demographics. Modern users expect a seamless and secure digital experience, and alternative logins can cater to those needs.
Social Login Options
Social logins, such as using a Facebook or Google account, offer a convenient way for users to access Spotify. This method eliminates the need to remember and manage additional usernames and passwords, which reduces the risk of account compromise. Many users already trust these platforms, so associating accounts provides a layer of security and ease.
- Advantages: Reduced password management burden, improved user experience, potential for faster onboarding, increased user engagement.
- Disadvantages: Potential security risks if the user’s social media account is compromised, privacy concerns regarding data sharing with third-party platforms, limitations on user control over the login process.
Fingerprint-Based Authentication
Fingerprint-based logins are a more secure and convenient alternative to traditional passwords. This biometrics-based method offers a higher level of security, as it relies on unique physiological characteristics. Users can verify their identity with a quick scan, making the login process both convenient and secure.
- Advantages: High security due to the unique nature of fingerprints, increased convenience compared to traditional passwords, reduces the risk of account takeovers due to compromised passwords.
- Disadvantages: Implementation complexities and potential user resistance to the concept of biometric authentication, issues with device compatibility, privacy concerns regarding the storage and handling of biometric data.
Integration Strategies
Integrating alternative login methods into Spotify’s existing system requires careful planning and execution. A phased rollout approach is recommended, allowing for testing and refinement. This phased approach ensures minimal disruption to the user base.
- Step 1: Identify the most suitable alternative login method based on Spotify’s target audience and technical capabilities.
- Step 2: Implement the selected method using secure and robust APIs provided by the third-party platforms (e.g., Facebook, Google, or fingerprint authentication providers).
- Step 3: Thoroughly test the integration to ensure proper functionality and security, with particular attention paid to user experience.
- Step 4: Implement user support and education on the new login methods.
Comparative Analysis of Login Methods
The table below provides a concise comparison of the different login methods, highlighting their strengths and weaknesses.
| Login Method | Advantages | Disadvantages | User Experience Impact |
|---|---|---|---|
| Username/Password | Traditional, widely understood | Security vulnerabilities, password management issues | Can be cumbersome, prone to errors |
| Social Login | Convenience, reduced password burden | Privacy concerns, security risk if social account compromised | Fast, streamlined, but may involve data sharing |
| Fingerprint Authentication | High security, convenient | Implementation complexity, device compatibility issues, privacy concerns | Secure, quick, but requires user adoption |
Last Word
In conclusion, logging into Spotify, while seemingly straightforward, involves a multitude of factors from UX to security, technology, and user support. This comprehensive overview has explored the intricacies of the process, highlighting the importance of each component for a positive user experience. By understanding the nuances of the login process, Spotify can continuously refine and improve its service for a growing user base.

Leave a Reply