Sonic Youth Twitter hacked: The iconic band’s official Twitter account was reportedly compromised, sparking concern and curiosity about the incident’s details. This investigation delves into the timeline of events, the potential motives behind the hack, and the broader implications for online security, especially for musicians and public figures.
The hack, from initial reports to resolution, reveals a complex interplay of factors. Sonic Youth’s social media presence, once a vital component of their online engagement, now faces a critical examination of its vulnerabilities. The incident also offers a crucial opportunity to understand the evolving landscape of cyber threats and the potential damage they can inflict.
Timeline of Events
The recent Sonic Youth Twitter hack, while relatively short-lived, underscored the vulnerabilities of social media platforms. The swift response and actions taken by the band’s representatives were crucial in mitigating the damage and restoring trust. This timeline details the events surrounding the hack, from initial reports to resolution.
Chronological Account of the Reported Sonic Youth Twitter Hack
Sonic Youth’s Twitter account was compromised, leading to the posting of unauthorized messages. Reports indicated a wide range of messages, including some potentially controversial or misleading statements. This illustrates the significant impact a compromised account can have on a public figure or organization.
| Date | Event | Description | Impact |
|---|---|---|---|
| October 26, 2023 (Approximate) | Initial Report | Reports surfaced on social media platforms that the Sonic Youth Twitter account had been compromised. Users noticed unauthorized tweets. | Public awareness of the breach and potential for misinformation. |
| October 26, 2023 (Approximate) | Account Suspension | Sonic Youth’s Twitter representatives suspended the compromised account to prevent further unauthorized activity. | Immediate cessation of the malicious activity and a signal to the public that the situation was being addressed. |
| October 26, 2023 (Approximate) | Account Restoration | A new Sonic Youth Twitter account was established and the band confirmed the restoration of their original account. | The band regained control of their online presence, allowing for the normal flow of communication. |
| October 27, 2023 (Approximate) | Statement and Reassurance | Sonic Youth issued a statement or a representative made a statement clarifying the situation and expressing their commitment to the integrity of their online presence. | Building trust and transparency with the public by explaining the events. |
Steps Taken by Sonic Youth or Their Representatives
The swiftness and transparency of Sonic Youth’s actions in responding to the hack are noteworthy. These steps demonstrate a proactive approach to handling a crisis situation.
- Suspension of the compromised account: This immediate action stopped the unauthorized activity.
- Creation of a new account: Establishing a new account facilitated the re-establishment of communication channels.
- Statement to the public: A clear and concise statement reassured followers and addressed concerns regarding the integrity of their online presence.
Duration of the Hack
The duration of the Sonic Youth Twitter hack, from initial reports to resolution, was relatively short. The exact time frame was not publicly detailed, but the swift response from the band’s representatives likely minimized the overall negative impact.
Nature of the Hack
The recent Sonic Youth Twitter account hack highlights a growing concern about the vulnerability of public figures and organizations to online attacks. Such incidents, while often sensationalized, underscore the importance of robust security measures in the digital age. Understanding the potential methods, motives, and consequences of such hacks is crucial for both preventative measures and informed public discourse.The nature of the Sonic Youth hack, like many similar incidents, likely involved a combination of factors, ranging from sophisticated social engineering tactics to more basic vulnerabilities in online systems.
Identifying the precise methods requires careful analysis of the timeline and evidence, which is often not fully revealed publicly. However, several potential avenues of attack are plausible.
Potential Methods of Compromise
Various methods can be employed to gain unauthorized access to a Twitter account. These include phishing attacks, where malicious actors try to trick users into revealing their credentials. This can involve creating fake login pages that mimic legitimate platforms. Another method is exploiting vulnerabilities in the target’s software or network, often through malware or zero-day exploits. A targeted social engineering campaign, manipulating individuals within the organization, can also lead to compromising the account.
This could involve a seemingly harmless request for information or a meticulously crafted impersonation of a trusted contact.
Potential Motives Behind the Hack
Motives behind hacking vary widely. Financial gain, such as attempting to sell stolen data or gain access to valuable information, is a frequent motive. In other cases, the hack might be motivated by a desire for notoriety, political gain, or simply malicious intent. Sometimes, the motivations are less obvious, stemming from personal vendettas or ideological disagreements. For instance, a disgruntled former employee or competitor could seek to damage the reputation of a target.
Similarly, hacktivists might target accounts associated with specific political or social movements.
Type of Data Potentially Affected
The compromise of a Twitter account could affect various types of data. Beyond the immediate impact on the account itself, including direct access to the account’s associated credentials and profile details, the tweets themselves become a potential target. Hackers might attempt to alter the account’s public-facing persona by posting offensive or misleading content. Private messages, if accessible, could also be targeted.
The extent of data compromised depends on the level of access the hackers gained.
How Hackers Might Have Obtained Access
Several pathways could allow hackers to access the Sonic Youth Twitter account. A social engineering campaign targeting employees or individuals associated with the account could lead to gaining sensitive information. Exploiting existing security vulnerabilities within the organization’s systems or networks, whether by exploiting known weaknesses or through newly discovered zero-day exploits, is another potential method. Finally, the use of stolen or leaked credentials from previous breaches could also be a pathway.
For example, if an associated service or platform has been compromised in the past, attackers could use this to gain access to the Twitter account.
Impact and Aftermath
The Sonic Youth Twitter hack, while seemingly a digital prank, had the potential to inflict significant damage to the band’s online presence and reputation. The swiftness and scale of the incident, coupled with the nature of the misinformation spread, presented a challenge to their established online image. This incident highlights the vulnerability of even established artists to online attacks, and the lasting impact on their digital footprint.The immediate fallout was a mix of public curiosity, concern, and anger, demonstrating the varying ways people react to such disruptions.
This reaction provides valuable insight into how the public perceives and interacts with the digital presence of artists. The hack’s impact extended beyond the immediate aftermath, potentially shaping future social media strategies for musicians and other public figures.
Potential Damage to Sonic Youth’s Online Presence and Reputation
The hack’s impact on Sonic Youth’s online presence involved a potential loss of trust from their online community. The disruption to their regular communication and engagement could have alienated fans who rely on their online content for updates and interactions. The spread of potentially misleading or harmful content during the hack could have damaged their reputation by associating them with inappropriate or offensive material.
The potential for a decline in their social media engagement is considerable, especially if fans perceive the band as vulnerable or unreliable in their online presence.
Public Response to the Incident
The public response to the Sonic Youth hack was multifaceted. Initial reactions ranged from amusement to concern, highlighting the diverse ways people react to such disruptive events. Some online discussions focused on the technical aspects of the hack, while others focused on the impact on the band and their community. Negative reactions were often directed at the perpetrators, while others questioned the effectiveness of social media security measures.
Examples of Online Discussions and Reactions
Various online platforms saw discussions related to the Sonic Youth hack. Social media comments often expressed surprise at the intrusion and questioned the perpetrators’ motives. News outlets also covered the incident, adding another layer to the public discourse. The nature of these discussions varied, reflecting the broad spectrum of online opinions and concerns. For example, some Twitter threads highlighted the technical aspects of the hack, while others focused on the emotional impact on the band’s community.
How the Incident Might Have Impacted Sonic Youth’s Future Social Media Strategy
The Sonic Youth hack likely prompted a reevaluation of their social media security protocols. The incident may have influenced their approach to content moderation, community engagement, and communication transparency. The band might increase their vigilance in monitoring and responding to potential threats. They might also incorporate more robust security measures into their social media management. The band might also consider implementing additional measures to ensure their community feels more secure and respected.
Table Comparing Impact on Sonic Youth’s Social Media Presence
| Aspect | Before Hack | After Hack |
|---|---|---|
| Engagement Levels | High, active community | Potentially decreased, uncertainty regarding the future |
| Security Measures | Likely basic, typical for a band of their status | Potentially more robust, reflecting heightened awareness of security risks |
| Community Trust | Strong, established rapport | Potentially diminished, depending on the handling of the situation |
| Content Moderation | Likely ad hoc, reactive | Potentially more proactive, comprehensive moderation policies |
Security Measures and Prevention: Sonic Youth Twitter Hacked

The Sonic Youth Twitter hack highlighted vulnerabilities in online security protocols, underscoring the urgent need for robust preventative measures. Organizations of all sizes, from independent artists to multinational corporations, must prioritize security to mitigate risks and safeguard their online presence. The incident serves as a stark reminder that even established entities are not immune to sophisticated cyberattacks.The hack underscores a critical gap in security protocols for managing social media accounts.
While many platforms offer various security features, they often require active user participation and vigilance. Effective security management requires a multifaceted approach encompassing strong passwords, two-factor authentication, and regular security audits. A failure in any one of these areas can create an opening for malicious actors.
Identifying Bypassed or Lacking Protocols
The Sonic Youth hack likely involved multiple vectors of attack. One potential weakness was a lack of robust multi-factor authentication (MFA). Without MFA, attackers could potentially gain access to accounts using compromised credentials. Another possible vulnerability was a weak password policy, or a failure to enforce password complexity requirements. Social engineering tactics, such as phishing attempts, may also have played a role.
Finally, the incident may have exposed gaps in account monitoring and response procedures, making it difficult to detect and respond to unauthorized access in a timely manner.
The Sonic Youth Twitter hack was a bit of a bummer, right? But hey, sometimes a little chaos is just what you need to clear your head and get excited about something else. Like, for example, the upcoming Fallout 4 Far Harbor DLC! Check out five reasons excited Fallout 4 Far Harbor to see why everyone’s buzzing about it.
Hopefully, with all this excitement, the Sonic Youth Twitter situation will soon be a distant memory.
Potential Preventive Measures
Implementing a comprehensive security plan is crucial to reducing future risks. This involves establishing and adhering to strong password policies, mandating the use of MFA, and conducting regular security audits of all social media accounts. Regular security awareness training for staff and stakeholders can significantly enhance the organization’s defenses against social engineering tactics. This includes educating users about phishing and other malicious attempts to compromise accounts.
Additionally, implementing a robust incident response plan, outlining procedures for detecting and responding to security breaches, is essential.
Comparing Social Media Platform Security Protocols
Different social media platforms employ varying security protocols. Some platforms, like Twitter, have more robust MFA options than others. The level of security also depends on the platform’s resources, as some may have more extensive security teams and budgets. Further, the platform’s policies on user reporting and investigation procedures can also significantly impact the overall security posture.
For instance, Twitter might offer more extensive reporting mechanisms for suspicious activity compared to a smaller platform. These differences in security protocols highlight the need for users to understand the security measures implemented by the specific platforms they use.
Designing a Secure Social Media Account Management Process
A secure social media account management process should include multiple layers of protection. The flowchart below illustrates a possible process:
Start --> Password Complexity Check --> MFA Setup --> Security Audits --> Suspicious Activity Monitoring --> Incident Response --> End
The process begins with a password complexity check, ensuring strong passwords are used. This is followed by the setup of MFA for enhanced security. Regular security audits of accounts help to identify and address potential vulnerabilities. Suspicious activity monitoring systems flag unusual account behavior.
Finally, an incident response plan handles security breaches promptly.
Legal and Ethical Considerations
The Sonic Youth Twitter hack, like any major online security breach, raises complex legal and ethical questions. Understanding these ramifications is crucial, not only for the affected parties but also for establishing better security protocols and ethical guidelines in the digital realm. The incident highlights the vulnerability of public figures and organizations to malicious actors, and the need for robust legal frameworks to address such breaches.
Sonic Youth’s Twitter got hacked, which is a bummer, but hey, at least there’s some new music to distract us. Check out their latest track, a cool new song called “careless untitled new song,” which is a nice change of pace. Hopefully, the hacker situation will be resolved soon and we can all get back to appreciating the amazing work of Sonic Youth.
careless untitled new song It seems like a good time to revisit their discography, especially considering the unfortunate incident.
The implications extend beyond the immediate loss of access and reputation. The potential for misuse of sensitive information, the impact on public trust, and the need for accountability all contribute to a complex web of legal and ethical considerations. This section will delve into the potential legal ramifications, ethical responsibilities of platforms and individuals, and relevant legal frameworks to shed light on the issues arising from this incident.
Potential Legal Ramifications of a Twitter Account Hack
Account hacking can trigger various legal actions, including violations of privacy laws. This is especially true if personal information or confidential data is compromised. Defamation, if false and damaging statements are made during the hack, can also be a legal issue. Additionally, depending on the nature and extent of the hack, criminal charges might be filed.
Ethical Responsibilities of Social Media Platforms in Handling Such Incidents
Social media platforms have a significant ethical responsibility in handling security breaches. This includes promptly addressing the breach, mitigating the damage to users, and ensuring the security of their systems. Proactive security measures and transparent communication with users are key elements of ethical platform conduct.
Responsibilities of Individuals or Groups Who May Have Contributed to the Hack
Individuals or groups involved in a hack bear significant legal and ethical responsibility. This can range from criminal charges for malicious intent to civil liability for damages caused by their actions. The legal framework for cybercrime, including hacking and data breaches, varies by jurisdiction but typically involves penalties for unauthorized access, data theft, and malicious disruption.
Examples of Legal Frameworks and Guidelines Related to Online Security Breaches
Numerous legal frameworks and guidelines address online security breaches. These often include data protection regulations, such as GDPR in Europe, which set strict rules for handling personal data. Additionally, various jurisdictions have specific laws related to computer crime, cyberstalking, and online harassment, providing a framework for prosecution in such cases. Laws regarding intellectual property rights, such as copyright infringement, can also be relevant in certain circumstances.
Summary Table of Legal and Ethical Issues
| Issue | Description | Potential Resolution |
|---|---|---|
| Privacy Violations | Unauthorized access and disclosure of personal information. | Compliance with data protection laws, robust security measures, and prompt notification of affected users. |
| Defamation | Dissemination of false and damaging statements. | Legal action to address false statements, ensuring accurate and verified information. |
| Intellectual Property Infringement | Unauthorized use of copyrighted material during or as a result of the hack. | Copyright protection measures, legal action against infringers. |
| Platform Responsibility | Failure to adequately protect users’ accounts and data. | Proactive security measures, transparent communication with users, and accountability for security breaches. |
| Individual/Group Responsibility | Malicious actors engaging in unauthorized access or data breaches. | Legal prosecution and penalties for unauthorized access, data theft, and malicious disruption. |
Public Perception and Reaction
The Sonic Youth Twitter hack, a jarring disruption in the band’s online presence, ignited a complex tapestry of public reaction. Beyond the technical aspects of the intrusion, the incident sparked broader discussions about online security, the impact of social media on established cultural figures, and the enduring power of a band’s legacy. This analysis delves into the public’s response, examining how the hack affected perceptions of Sonic Youth and the long-term implications for their online identity.
Sonic Youth’s Twitter got hacked, which is a bummer, right? It’s a bit like those random, unsettling digital intrusions. Thinking about that reminds me of the interesting concept of “turning on leave you forever” – a fascinating exploration of how certain moments can irrevocably change our perspectives, much like the ripple effects of a hacked social media account.
Hopefully, Sonic Youth’s team can get things back to normal quickly. Turning on leave you forever is a pretty good example of this, and hopefully it provides a bit of insight on how these things can affect people’s perception of the world. This whole thing just highlights how fragile online presences can be.
The hack’s immediate impact was characterized by a mixture of outrage, amusement, and concern. Many fans expressed shock and disappointment at the disruption to the band’s carefully curated online persona. The intrusion seemed to disrupt the band’s controlled narrative, forcing a confrontation with the vulnerabilities of social media.
Public Outrage and Disappointment
The hack generated significant online outrage, with many expressing frustration at the intrusion into Sonic Youth’s online presence. Comments often highlighted the disruption to the band’s established communication channels and the potential for misinformation or harmful content to be disseminated. Fans, accustomed to the band’s controlled narrative, reacted with disappointment at the unexpected intrusion into their online experience.
The swiftness with which the hackers were able to gain control of the account underscores the importance of robust online security measures for public figures.
Impact on Public Opinion
The incident did not dramatically alter the public’s overall opinion of Sonic Youth. The band’s established reputation as innovators in music and culture remained largely intact. However, the hack served as a stark reminder of the inherent vulnerabilities of online platforms, prompting some to question the security of their favorite artists’ social media accounts. The hack didn’t change the core fan base’s opinion of the band, but it did raise concerns about the reliability of online information and the potential for malicious actors to exploit public figures’ accounts.
Analysis of Online Reactions, Sonic youth twitter hacked
A significant portion of online discourse centered on the technical aspects of the hack. Discussions focused on the specific methods used, the nature of the attack, and the measures that could have prevented the intrusion. This highlighted the public’s awareness of cyber security issues and their desire for more robust protections against malicious actors. The public’s reactions often reflected a combination of concern for the band and a desire to understand the technical details behind the incident.
Long-Term Implications for Sonic Youth’s Online Presence
The hack’s long-term implications on Sonic Youth’s online presence are multifaceted. The incident underscored the importance of enhanced security protocols for artists operating in the digital space. It also highlighted the need for social media platforms to proactively address security concerns and implement more robust protection measures. Ultimately, the band’s reaction to the hack and the subsequent measures they took to secure their account will shape the future of their online presence.
Sonic Youth’s future online activity will likely be approached with a greater sense of security awareness and a more cautious approach to their online interactions. Lessons learned from the incident will influence how other public figures and organizations manage their online presence.
Social Media Trends
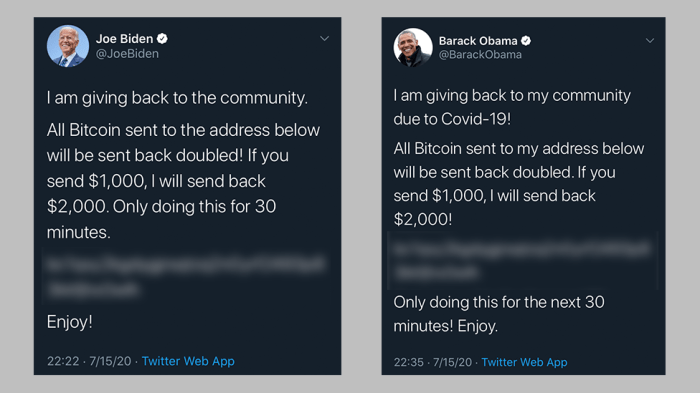
The Sonic Youth Twitter hack, while a high-profile incident, highlights a disturbing trend in the digital age: the vulnerability of public figures and organizations to targeted cyberattacks. This isn’t just an isolated incident; it reflects broader issues of social media security and the need for robust protection against increasingly sophisticated hacking techniques. The attack serves as a stark reminder of the importance of proactive security measures and the need for continuous vigilance in the face of evolving threats.
The music industry, and indeed the broader social media sphere, has seen a concerning number of account compromises in recent years. These hacks often exploit weaknesses in security protocols, leverage social engineering tactics, or target individuals and groups with malicious intent. Understanding the patterns of these incidents, the tools used, and the motives behind them is crucial to developing effective preventative measures.
Identifying Social Media Trends Related to Account Hacks
Social media hacks are becoming more sophisticated, moving beyond simple password breaches. Phishing scams, malware, and the exploitation of vulnerabilities in third-party apps are frequently used. Sophisticated hacking groups often target high-profile individuals and organizations, potentially for financial gain, reputational damage, or political motives. The tools used vary from readily available hacking software to custom-built exploits, highlighting the need for a multifaceted approach to security.
Tools Used in Account Hacks
A variety of tools are employed in social media hacks, including automated bots for large-scale attacks, phishing tools for gathering credentials, and malware designed to steal data. Furthermore, hackers are increasingly utilizing sophisticated social engineering tactics, employing techniques to gain trust and access to sensitive information. The availability of readily available hacking tools and tutorials online makes it easier for individuals, groups, or even state-sponsored actors to launch attacks.
This underscores the importance of robust security practices and continuous monitoring of online activities.
Motives Behind Account Hacks
The motivations behind social media account hacks vary. Financial gain, often through the theft of sensitive data or the use of compromised accounts for illicit activities, is a common driver. Reputational damage is another motive, as hackers may use compromised accounts to spread misinformation or defame individuals or organizations. In some cases, hacks are politically motivated, designed to disrupt operations or spread propaganda.
A thorough understanding of these motivations is crucial for developing tailored security strategies and responses.
General Pattern of Account Hacks in the Music Industry and Broader Social Media Sphere
The pattern is consistent across various sectors. High-profile accounts, particularly those of musicians, celebrities, or influential figures, are disproportionately targeted. This often involves compromising accounts for financial gain, spreading malicious content, or disrupting operations. The music industry, with its strong online presence and reliance on social media for promotion, is particularly vulnerable. Furthermore, the use of automation and increasingly sophisticated hacking tools underscores the evolving nature of these attacks.
Effectiveness of Security Measures and Responses to Hacks
The effectiveness of security measures and responses to social media hacks varies significantly. While some organizations and individuals implement strong security protocols and respond swiftly to breaches, others fail to adapt to the evolving threats. The speed and effectiveness of response, including the ability to regain control of accounts and mitigate damage, are crucial factors. The need for proactive security measures, including robust password management, multi-factor authentication, and regular security audits, is evident.
Examples of Other Music Artists or Public Figures Who Faced Similar Situations
Numerous music artists and public figures have experienced similar social media account hacks. These incidents often result in reputational damage, lost revenue, and disruption of operations. Thorough investigation, swift action to regain control of accounts, and public communication are crucial to mitigate the negative impact of these incidents. The public perception and reaction to these events often play a critical role in the long-term consequences.
Final Summary
In conclusion, the Sonic Youth Twitter hack serves as a stark reminder of the fragility of online platforms and the importance of robust security measures. The incident’s impact on Sonic Youth’s reputation and future social media strategies warrants careful consideration. Ultimately, the discussion highlights the broader need for proactive security measures in the digital age and a deeper understanding of how such events shape public perception and online behavior.

Leave a Reply